
Using Tor bridges in hostile environments
In some environments, your ISPs might be trying to prevent you from accessing Tor. Or accessing Tor openly might be a safety risk.
In those cases, it might be necessary to use Tor bridges to connect to the Tor network (see Tor Documentation and Whonix Documentation).
Bridges are special Tor entry nodes that are not listed on the Tor public directory. Some of those are running on people running the Snowflake Browser extension while others are running on various servers around the world. Most of those bridges are running some type of obfuscation method called obfs4.
Here is the definition from the Tor Browser Manual: “obfs4 makes Tor traffic look random and prevents censors from finding bridges by Internet scanning. obfs4 bridges are less likely to be blocked than its predecessor, obfs3 bridges”.
Some of those are called “Meek” bridges and are using a technique called “Domain Fronting” where your Tor client (Tails, Tor Browser, Whonix Gateway) will connect to a common CDN used by other services. To a censor, it would appear you are connecting to a normal website such as Microsoft.com. See https://gitlab.torproject.org/legacy/trac/-/wikis/doc/meek for more information.
As per their definition from their manual: “meek transports make it look like you are browsing a major web site instead of using Tor. meek-azure makes it look like you are using a Microsoft web site”. This is a type of “domain fronting”.
Lastly, there are also bridges called Snowflake bridges that rely on users running the snowflake extension in their browser to become themselves entry nodes. See https://snowflake.torproject.org/.
First, you should proceed with the following checklist to make sure you cannot circumvent Tor Blocking (double-check) and try to use Tor Bridges (https://bridges.torproject.org/):
-
(Recommended if blocked but safe) Try to get an obfs4 bridge in the Tor connection options.
-
(Recommended if blocked but safe) Try to get a snowflake bridge in the Tor connection options.
-
(Recommended if hostile/risky environment) Try to get a meek bridge in the Tor connection options (might be your only option if you are for instance in China).
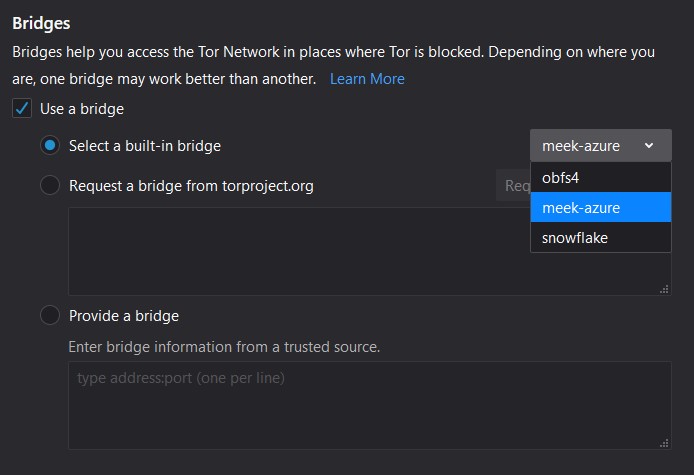
(Illustration from Tor Browser Bridge Configuration)
If none of those build-in methods are working, you could try getting a manual bridge either from:
-
https://bridges.torproject.org/bridges?transport=meek (for a meek bridge)
-
https://bridges.torproject.org/bridges?transport=obfs4 (for an obfs4 bridge)
This website obviously could be blocked/monitored too so you could instead (if you have the ability) ask someone to do this for you if you have a trusted contact and some e2e encrypted messaging app.
Finally, you could also request a bridge request by e-mail to [email protected] with the subject empty and the body being: “get transport obfs4” or “get transport meek”. There is some limitation with this method tho as it is only available from a Gmail e-mail address or a Riseup.net (https://riseup.net/) e-mail address.
Hopefully, these bridges should be enough to get you connected even in a hostile environment.
If not, consider Accessing the internet as safely as possible when Tor and VPNs are not an option
Source: The Hitchhiker’s Guide to Online Anonymity, written by AnonyPla © CC BY-NC 4.0
