.jpg)
A Complete Guide to Virtual Private Networks (VPNs)
There are very few locations where I actually trust connecting directly to the Internet. I don’t even do things like online banking or logging into my Bitwarden from work because the connection is open (not secured with a password/encryption) and thus much more susceptible to attack from an outsider. My home connection is likely the most secure because it is something that I have personally setup and am able to monitor, but even then, the modem that our ISP supplies that doubles as our WiFi router doesn’t provide the best possible security.
This is where Virtual Private Networks come into play. If chosen and set up correctly, they ensure us a secure, private, and often anonymous connection to the open Internet. Meaning we can browse freely without restrictions and free from surveillance. For the most part, those reading this won’t have any serious reason to avoid surveillance, but people have a right to privacy and shouldn’t be snooped on. Even if it is just by the sysadmin for the free WiFi at Starbucks. The issue comes down to picking a VPN that suites your needs. Some offer lots of locations globally, others a really great rate and awesome prices annually. I tend to root for and use the providers that offer the best privacy, security, and anonymity, even if it means paying a little bit more. Often times, the cheaper providers are only able to provide such great prices because they pack their servers and don’t “really” concern themselves with being all too private. So lets take a look from the perspective of someone who needs top notch security, spyproof privacy, and a high level of anonymity by going through some of the providers I have researched to be the best in these areas.
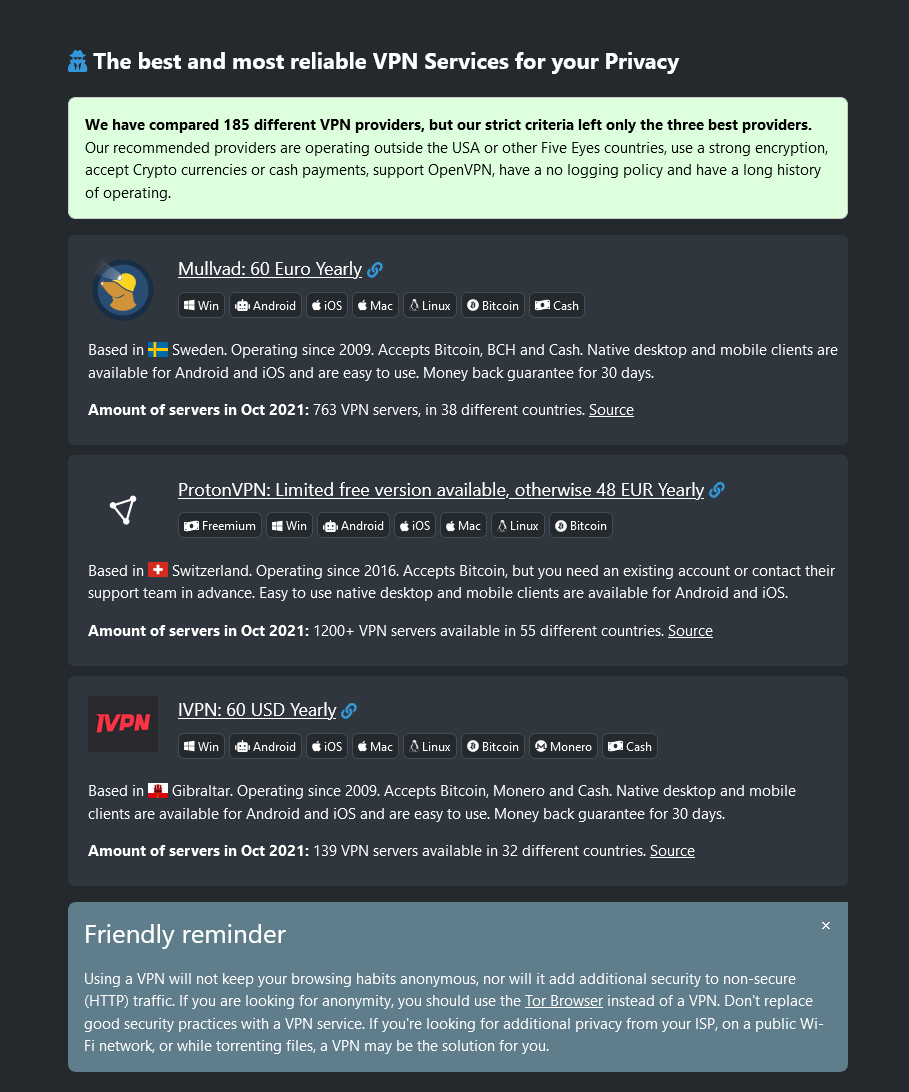
See: The best and most reliable VPN Services for your Privacy on PrivacyTools.io
Ideally, we are going to want a provider that isn’t based in one of the “5 Eyes Countries” (https://www.privacyinternational.org/press-release/51/privacy-international-launches-international-campaign-greater-transparency-around). This means it cannot be based out of Canada, The United States, The United Kingdom, Australia, or New Zealand due to their agreement to share information with one another without much question. They tend to have intelligence agencies (Like the NSA and GCHQ) that do a fair amount of data mining and surveillance on the individuals within their country for “matters of national security”. I would also caution you to stay away from anything listed inside of the “14 Eyes Countries” if you were relying on this provider for your personal safety. The provider you chose should also NOT provide the option for a dedicated IP address. Shared-IPs are strictly the way to go if you want maximum anonymity because it doesn’t single out your incoming IP and matching it with the VPNs outgoing IP. Harder to log/trace, but definitely not impossible.
Accepted payment methods are also a consideration you need to not take lightly. You obviously wouldn’t want to pay with your PayPal or Credit Card if you were looking for full-scale anonymity. Well-mixed bitcoin that doesn’t link back to you, cash in mail, and PaySafeCards are all methods of payment that are considered to very anonymous if done correctly. Encryption and protocols offered by the VPN Company should also be considered before making a purchase. You will often see the term “Military Grade Encryption” when you are out shopping for a good provider. Generally this just means they employ AES-256 and 4096 bit RSA keys but checking to see if they offer Perfect Forward Secrecy and good Curves for ECHDE Keys is important (http://vincent.bernat.im/en/blog/2011-ssl-perfect-forward-secrecy.html , https://www.perfectforwardsecrecy.com/ , https://safecurves.cr.yp.to/).
Diving a little deeper into the providers as you shop around, you should check out the server locations they offer and see if they are in jurisdictions that you are happy to be connecting to. This would be a good time to see if any of the sites you want to connect to only work in certain countries (like Hulu, Pandaora, Netflix, etc). As well, like I mentioned above with SSL certificates and how you can check to make sure the site is implementing strong standards for HTTPS, you should be checking the VPN provider's site to see what kind of SSL they are using. If they don’t get a grade of A, I would caution against using them as a provider because it shows that they clearly either can't take the time to get a good SSL score (if even just for the promotion) or that they aren’t knowledgeable enough to attain it; a fact that could point towards their service being held up by mountains of false claims. It is also good to see what kind of protocols they are promoting and not just what they are supporting. Most of the good providers will at least ship out a client for Windows and have added features like killswitches and firewalls to stop DNS/IP leaks. However, there are a few providers that I saw who were saying that connecting over L2TP was the best option when it definitely is not. To read more about the different protocols, you can see this link: https://www.ivpn.net/pptp-vs-ipsec-ikev2-vs-openvpn-vs-wireguard/
Below are reviews of the 4 VPN Providers that I have used and trust. You can also check out this link to a website (formerly Google Doc) that was created by ThatOnePrivacyGuy. It documents a lot more providers than just these 3 but is something that has backed my decisions to promote these companies.
IVPN
To kick the personal reviews off, I have decided to go with the VPN provider that I have been using since early 2013. IVPN, originally incorporated in Malta but recently making the move to Gibraltar due to changing privacy laws, is dedicated to your privacy. They offer 12 countries and a total of 19 servers as of April 2016, which is a fairly small network compared to many other providers. However, I am happy with the locations they have chosen. You can see the full list of locations here: https://www.ivpn.net/status. They market themselves on Twitter as “IVPN is an online privacy and security service” which to me is a step up from all the Military Grade Encryption and Non-Logging talk that goes around in the VPN community all too much. They state very clearly in their privacy policy (https://www.ivpn.net/privacy) the information that is and isn’t logged. The nice thing about connections to IVPN servers is their multihop technology, which allows you to connect through two separate IVPN servers before hitting the open Internet. This gives you as a user more anonymity, as both servers would need to be compromised to compromise your identity; unless they turned on logging of course. Their administration team also informed me that all the VPN servers are running from RAM so everything written is only temporary before being wiped. As a user, I cannot confirm this – but I do trust their word. Hopefully that isn’t a misplaced trust. The encryption protocols used are openly outlined in their “18 Questions to ask your VPN Service Provider” answers on their Support Page (https://www.ivpn.net/knowledgebase/108/Answers-for-18-Questions-to-ask-your-VPN-Service-provider.html). They state that they use AES-256 with 4096 bit RSA keys across the board, which they consider to be "Paranoid Encryption". I would be interested to find out what their thoughts are on post-quantum cryptography. Upon looking through their OpenVPN files given to the user to download, I was able to determine that they are using TLS-DHE-RSA-WITH-AES-256-CBC-SHA:TLS-DHE-DSS-WITH-AES-256-CBC-SHA:TLS-RSA-WITH-AES-256-CBC-SHA for the TLS cipher suite so you can rest assured that Perfect Forward Secrecy DOES exist on IVPN. They are using the highest level of encryption currently possible for OpenVPN (apart from allowing DSS and SHA1 for older clients) so that is a very good thing. You can confirm the encryption used yourself by downloading the .ovpn files from their website and opening them in a text editor but this will not confirm that those same standards are being employed through their native apps. But really, why wouldn't they be?
As for payment and pricing, IVPN is definitely on the higher end at $100 USD for an annual subscription. But they do offer PayPal, Bitcoin, and cash in mail so two possibly anonymous methods of payment are provided and one very easy and renewing method (PayPal). Their plans give access to all servers which is a nice change from the VPN providers that split up their plans based on a bunch of different factors like speed, server locations, etc. Registering was easy and they didn’t ask for anything more than an email, password, and my payment. That meant no identifying information had to be given out. IVPN also provides a warrant canary on a monthly basis as a way to say, “Hey, we haven’t received any government gag orders” and an entire section of their website dedicated to pretty much being 100% anonymous while behind a VPN. I suggest you check it out, I have pulled a lot of my own knowledge from these write-ups: https://www.ivpn.net/privacy-guides
As a final note, I have done a lot of verifying with their administration team over PGP encrypted email (pretty awesome that they kept up fairly lengthy conversations with me in an encrypted form), so I have a lot of personal trust with the company. But me having a lot of personal trust doesn’t give you the go ahead to also give them a bunch of your trust. You should do your own research and ask your own questions to make sure they are the company that will suite your needs. I do commend them greatly for the work they are doing, but I do not place all my eggs in one basket. I have been really satisfied with their service over the years but am finding that in a very competetive market, it is difficult to list any one VPN service at the top.
Mullvad
This re-write of the Mullvad review was spawned due to serious changes in their company over the last 2 years since I begun writing this paper.
Mullvad is a provider that I am now coining as "no bullshit". They very clearly outline their service, company, and practices on their website without any of the "Security Threater" talk of Military Grady Encryption and ZERO logging practices. To start, their website claims: "For maximum security, we use physical, bare metal servers (no virtual servers) that are administrated and either owned or rented by us in carefully selected data centers." I did not have to dig around to get this information either. It is very conveniently placed on their Features page and easily accessible to anyone who is checking out their website. They also state very explicitely, the encryption used in the connections:
- Our data encryption is AES-256
- All our OpenVPN servers use 4096 bit RSA certificates (with SHA512) for server authentication
- All our OpenVPN servers use 4096 bit Diffie-Hellman parameters for key exchange
- All our OpenVPN servers use DHE for perfect forward secrecy
- OpenVPN re-keying is performed every 60 minutes
I feel that having this information stated so plainly on their website is a big plus for their ability to cut through the VPN bullshit and just give the reader the facts. However, they don't stop there. Their features page also explains that Mullvad accounts do not need any of your information to register; not even an email address. You just fill out a CAPTCHA and it generates you a string of characters that is used as both your username and password for connections. This, as well as a plethora of other information relating to the data they do and do not collect and store is best read here: https://mullvad.net/en/help/no-logging-data-policy/
Diving into their website a little deeper, you will find that they, like IVPN, publish "Privacy Guides" of sorts here: https://mullvad.net/en/help/guides/. Although these guides do not appear to be as "all-inclusive" as the ones published by IVPN, they are still a wonderful resource to have listed on their website. They are also one of the first providers I have checked out to be supporting the WireGuard Protocol for connection. Although it is only currently available for Linux, WireGuard implements some neat cryptography above and beyond just simple AES-256 and 4096 bit RSA - Namely: "Noise protocol framework, Curve25519, ChaCha20, Poly1305, BLAKE2, SipHash24, HKDF, and secure trusted constructions." Being able to use eliptical curve cryptography with VPN connections is wonderful.
One point that I did find of particular interest on their blog section of their website is their work towards Post-Quantum Cryptography and the introduction of a VPN in the future that would be able to withstand the imposing threat of Quantum Computing (https://mullvad.net/en/blog/2017/12/8/introducing-post-quantum-vpn-mullvads-strategy-future-problem/). To see a provider looking forward into the future, not for their own monetary gain, but for the privacy and security of their clientel is really great to see. I believe this work, parelling the work ProtonMail is doing with secure email, is crucial in developing technology that exceeds the minimums to go above and beyond.
Cryptostorm
Lastly, we come to a provider that I only really started looking into in around September of 2015. I was still very satisfied with IVPN but my subscription was coming to an end, which meant another long process of anonymizing a method of payment and I wanted to make sure that the company I was going to continue to support got the most stars in my personal ratings from my “shopping” online. I had heard some amazing things about the CS Network and wanted to see what they were all about in more in-depth than just browsing through their site like I had previously done a few years back.
The first thing you’ll notice when you go to Cryptostorm’s website is what many perceive as a mess that is difficult to follow, hard to read, but somewhat appealing. It is unlike any of the other providers and almost unprofessional; but that feeling of difference seems to draw me closer. Sort of like how Mullvad was so straightforward and minimalistic, the odd nature of Cryptostorm’s website tells a story of diversity. To start, they are a company that is “sort of” based out of Iceland but handles all of their financials out of Quebec in Canada (they don’t really have a straightforward location – wouldn’t this make it difficult to provide a subpoena to them?). Iceland is a good privacy centered country to be incorporated in (although they don’t have a central office anywhere) and I have always liked .is domains.
Navigating through their website was pretty difficult to acquire the information one might want when choosing a provider so I took to their IRC to get some of my questions answered. I was unfamiliar with token-based authentication before asking around and getting a more detailed response but to my knowledge, it replaces user/pass authentication with a generated token that must be hashed before use. This token is random; hashing it makes it even more random. So the server should never have any information about the users at all if they pay using anonymized Bitcoin (which is the preferred payment method that they offer). The encryption that is used is not clearly located on their site so one has to dig slightly deeper and head over to their GitHub to check out the .ovpn config files yourself. This is what is displayed:
ns-cert-type server
auth SHA512
cipher AES-256-CBC
replay-window 128 30
tls-cipher TLS-DHE-RSA-WITH-AES-256-CBC-SHA
tls-client
key-method 2
#log devnull.txt
#verb 0
#mute 1
The encryption used appears to be very high-grade using DHE for perfect forward secrecy, 256-bit AES, and SHA512. However, this doesn’t designate the size of RSA keys being used. After contacting one of the administrators about the encryption used, this was the reply email I received. Really goes to show you the quality that is provided by Cryptostorm when they are willing to go to this degree to provide for their customers.
A current work in development for Cryptostorm that would seriously decrease the risk of correlation attacks or the possibility of your IP ever getting leaked, encryption keys compromised, or identity exposed is known as Voodoo. You can read more about that up and coming idea on the GitHub page for it here: https://github.com/cryptostorm/voodoo.network
As far as a Warrant Canary, Cryptostorm does not offer one and doesn’t seem to have any plans to do so. Instead, they offer a “Privacy Seppuku Pledge” which is their way of saying we will shutdown, wipe the servers, delete everything, and play dead before giving up information about our customers.
Overall, I am very confident in the service provided by Cryptostorm and certain that an individual, with a moderate threat model, could receive maximum security, privacy, and anonymity from using their VPN. They are like the nerd at the front of the classroom that is incredibly smart, but very hard to relate with and understand. And I think that is a good thing!
See: The best and most reliable VPN Services for your Privacy on PrivacyTools.io