For starters, a threat-model could be defined as how an individual needs to be protected based on things like:
What is Privacy? Wikipedia describes privacy as “the ability of an individual or group to seclude themselves, or information about themselves, and thereby express themselves selectively” and I would largely agree that the definition provided fits the mold. Read more
You got it; your smartphone is an advanced spying/tracking device that: Read more
Whether it is Android, iOS, Windows, macOS, or even Ubuntu. Most popular Operating Systems now collect telemetry information by default even if you never opt-in or opted-out from the start. Read more
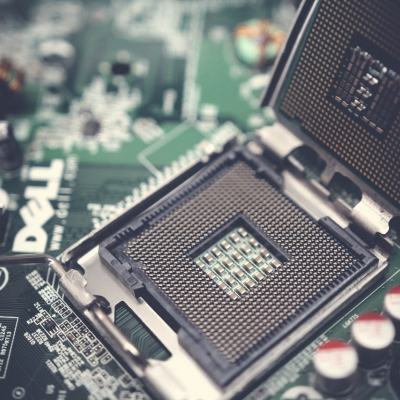
All modern CPUs are now integrating hidden management platforms such as the now infamous Intel Management Engine and the AMD Platform Security Processor. Read more
Your Bluetooth MAC is like the earlier MAC address except it is for Bluetooth. Read more
The MAC address is a unique identifier tied to your physical Network Interface (Wired Ethernet or Wi-Fi) and could of course be used to track you if it is not randomized. Read more
The IMEI (International Mobile Equipment Identity) and the IMSI (International Mobile Subscriber Identity) are unique numbers created by cell phone manufacturers and cell phone operators. Read more